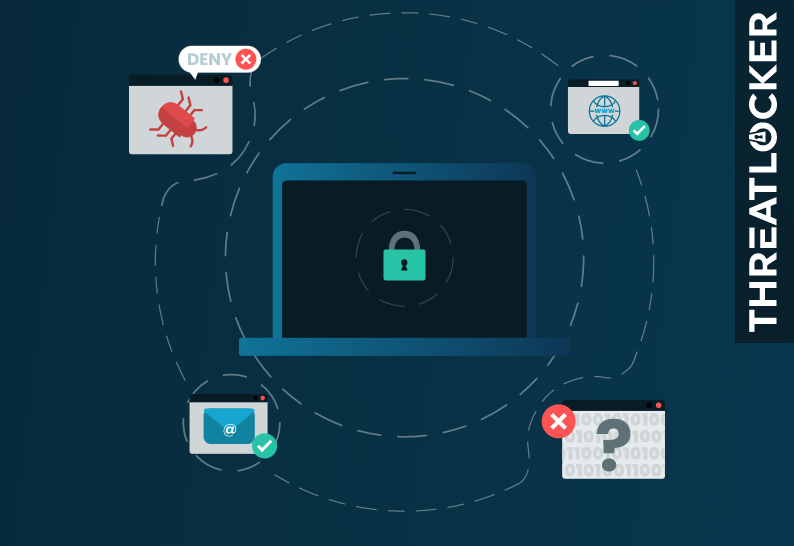
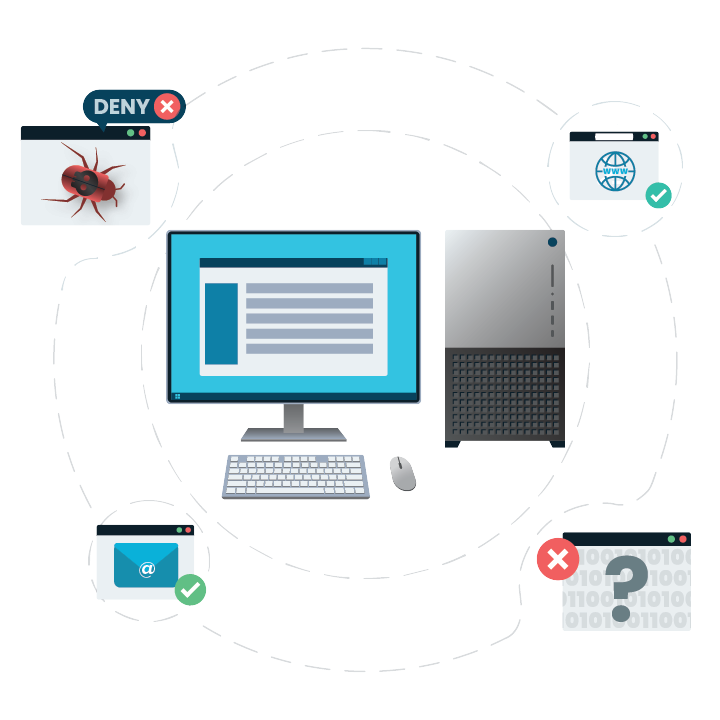
Allowlisting
Using the ThreatLocker® solution, you can deny any application from running on your device that is not a part of the Allowlist. This helps to mitigate and stop cyberattacks from happening on your devices or across your network.

Firewall-like Application Policies
A powerful firewall-like policy engine that allows you to permit, deny or restrict application access at a granular level.
Time-Based Policies
Permit access to applications for a specified amount of time. Automatically block the application after the policy has expired.
Built-In Applications
ThreatLocker® automatically adds new hashes when application and system updates are released, allowing your applications to update without interference while preventing updates from being blocked.